As the security of data becomes one of the most serious issues, a robust Security and Operations (SOC) team could be the solution to cybersecurity in the Healthcare industry. In the last two years, almost 90% of hospitals in the United States have reported a security breach. Cyber attacks cost the United States healthcare system at least $6.2 billion every year, and the most significant healthcare data breach affected a whopping 80 million people. In this article, we discuss why the sector is particularly vulnerable to cyber threats and what healthcare organizations can do to overcome this vulnerability.
Why do we need Security and Operations(SOC) in Healthcare?
While cybersecurity has become a rising concern across all industries in the recent past, the healthcare sector is particularly susceptible. There are many aspects to this.
- Healthcare data is valuable
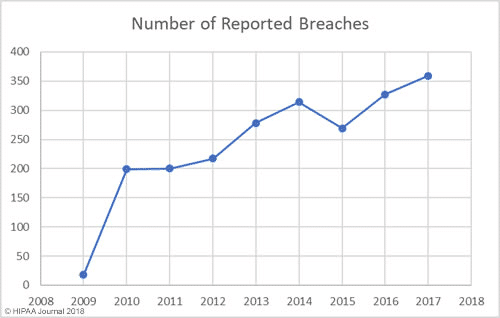
The first issue is that the healthcare industry stores enormous amounts of highly personal information about patients. This data is particularly useful in the black market and therefore highly attractive to cybercriminals. This patient data can be used for identity theft to get access to expensive medical devices, specialized medical services, and prescription drugs. It can also be used to obtain benefits like Medicaid and Medicare. Here is a graph which shows the rise in data breaches in the healthcare industry.Image Ref: https://www.hipaajournal.com/wp-content/uploads/2018/03/number-reported-healthcare-data-breaches.jpg[/caption]
- Healthcare data is critical
The second issue is that patient data can be the difference between life and death. For instance, cutting off access to a life-saving wearable device, mixing up a patient’s medication, or failure to treat a severe condition can all have serious consequences. This makes healthcare data very attractive to cybercriminals who hold the data for ransom. The healthcare sector faced 88% of all ransomware attacks in the USA last year. - Accessing Healthcare Data
Healthcare data needs to be obtained by a diverse range of people from patients and doctors to pharmacies and researchers. The data also needs to be located 24/7 across a variety of devices. Cybersecurity is increasingly being seen as a barrier to this complete and uninhibited data access. - State of Healthcare Technology
Another factor that exacerbates the situation is the state of technology in the healthcare sector. Most healthcare organizations don’t have the resources or the willingness to invest in upgrading their tech infrastructure. This makes them even more vulnerable to increasingly sophisticated cyber threats. Another reason is that the healthcare system has the additional burden of meeting the strict compliances of bodies like HIPAA.
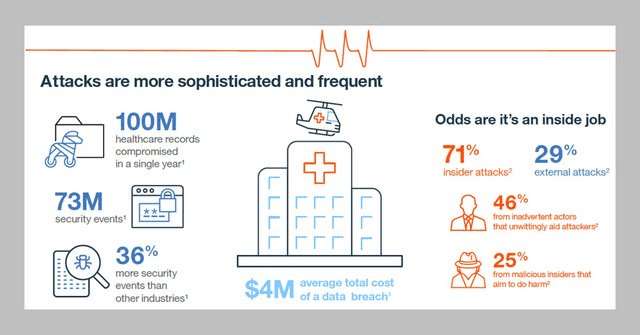
No wonder then, that the healthcare system across the world has faced some major security setbacks in recent years. These include the 2015 attack on Anthem where 78.8 million patient records were stolen and the breach of the Singapore government’s health database which affected 1.5 million patients. Here is an infographic by IBM that sheds light on some critical aspects of cybersecurity in healthcare.
How Are Cybersecurity Systems Handling These Attacks?
Earlier, cyber threats followed a more-or-less standard pattern, and corresponding cybersecurity measures were also run-of-the-mill. However, cyber threats are now becoming increasingly complex and sophisticated with the use of the latest technologies and extreme customization. As a result, cybersecurity teams and techniques have to be upgraded accordingly.
Most healthcare organizations continue to focus on network and endpoint security. However, these are known to be comparatively ineffective when it comes to new-age data breaches. Moreover, they can’t help secure the deployment of new technologies like cloud, big data, internet of things (IoT), and containers.
High costs and talent shortage have been standing in the way of implementing effective cybersecurity measures. However, the recent high-profile data breaches have made both customers more conscious about the issues surrounding data security. Fifty-eight percent of the respondents in an IOM survey said that they don’t believe their health information is adequately protected.
As a result, healthcare organizations can no longer afford any more delay in developing a comprehensive cybersecurity setup. The first step towards having an updated and useful cybersecurity arrangement is setting a Security and Operations Centre(SOC).
What Is a Security and Operations Centre(SOC) and Why Is It Important?
A Security and Operations Centre(SOC) is a facility that continually monitors an organization’s cybersecurity. SOCs are not a new concept. They have been a part of the military and national security organizations for years. The SOC detects, prevents, investigates, responds to, and analyses cyber threats. It uses both, the latest technologies, as well as the best practices and procedures, to make sure that the organization’s cybersecurity is up to date.
The SOC allows for a comprehensive approach to data security. With a SOC, an organization can go into the depths of the network to discover all the significant weaknesses and build an active detection system thereon. This will allow security functions to become more collaborative and faster. The SOC will be able to figure this out as soon as something wrong happens to the network and handle the situation appropriately.
How to Structure and Build a Security and Operations Centre(SOC)
Here are some key steps you need to follow to set up a Security and Operations Centre that is automated as much as possible and that works at scale.
- Develop a strategy to build your SOC. This includes assessing your current capabilities and identifying your key business objectives. It’s important to make sure the SOC also has a compelling ROI(Return on Investment).
- If you don’t have the resources for a full-scale SOC, start with the core functions. These include monitoring, detection, response, and recovery. Delay the non-core functions until your core functions are mature.
- Keep your SOC design rooted in practicality. Start with some critical use cases and design the initial solution for those use cases. Of course, the answer should be able to meet future needs also. Keep the scope narrow, to begin with. This will help reduce the implementation time and help you get started faster.
- Define your functional requirements based on your business objectives. Then, choose a SOC model based on these technical requirements.
Design the technical architecture for your SOC. This would include defining workflows, figuring out the areas for automation, and identifying the business and information systems to be integrated. - Choose your Threat Lifecycle Management platform. It’s important to make sure that all six phases of the threat lifecycle management framework are covered. These include collecting data, discovering threats, qualifying threats, investigating threats, neutralizing threats, and system recovery.
- Make sure your environment is secure before actual deployment. Ensure that the SOC staff devices are entirely safe and require strong authentication. Also, make sure remote access mechanisms are in place for both SOC staff and outsourced staff, if any.
- Deploy the solution. Make sure to bring up your log management infrastructure, onboard a minimum collection of data-critical resources, and onboard your security analytics and automation capabilities. Finally, start deploying end-to-end use cases from threat detection to response and recovery. Interoperability of the system is critical. It will help your team collect data from different sources and be able to take action and contain threats in alignment with your workflows.
- Incorporate threat intelligence feeds and automated inputs from different sources. This will help improve your SOC’s detection capabilities.
- Once your technology is set up, and your capabilities are deployed, begin with the implementation. Ensure you do so across the analytics and security automation and orchestration tiers. Make sure to test all use cases thoroughly, especially over some shifts and in between changes. Try to make the reliability and security of the solution as foolproof as possible.
- The final step is to ensure that you don’t leave the SOC on autopilot once it is operational. It requires ongoing fine-tuning and maintenance to keep it running. This includes tuning to improve detection capabilities, integrating other systems as inputs or outputs, and periodically reviewing the SOC staff, model, and requirements.
Best Practices to Keep in Mind
A SOC requires a significant investment of time, talent, and resources on the part of a healthcare organization. It’s important to keep certain best practices in mind to make sure that it is a productive investment.
- Remember that the SOC’s job is threat detection and control. They are not a help desk for your employees. Giving this additional responsibility to the SOC will overwhelm them and compromise their core threat-hunting function.
- The best SOC staff in the world will be useless without state-of-the-art tech infrastructure to support them. Make sure you give your SOC what they need whether it’s Firewalls, Endpoint Protection Solutions, Security Information, and Event Management (SIEM) Solutions, Security Probes or Data Collection Tools.
- Find the right solution based on your budget. If your organization doesn’t have the budget to invest in a full-scale SOC, don’t just give up on cybersecurity. You can collaborate with firms who provide managed cybersecurity solutions and
outsource SOC elements that you can use. - Have an incident response plan in place so that your SOC knows precisely what needs to be done when a security incident takes place. This includes informing the relevant teams including PR, legal, and various regulatory bodies.
Find the Right People for Your Security and Operations Centre(SOC)
A shortage of cybersecurity professionals across industries is a significant concern. A SOC can only succeed when it has the right experts in critical positions. These include:
- An incident responder who will perform an in-depth incident analysis.
- An incident hunter who is usually a subject matter expert.
- An analyst who will monitor alerts and the overall health of the sensors.
Given the scarcity of cybersecurity talent, it may also be worth it to hire an expert healthcare IT solution company who can help you build and manage the SOC.
The healthcare industry has been dragging its feet on cybersecurity for many years now. However, recent attacks have made it impossible to ignore the establishment of a robust and updated cybersecurity system. A comprehensive Security and Operations Centre(SOC) is the foundation for this system. As per an informal survey of healthcare providers, close to 60% are planning to or have already set up a SOC.
The Bottom Line
As mentioned, Cybersecurity is the most vulnerable area in healthcare. With technology driving so much, it is a matter of “when” and not “if” the attacks happen. It requires special planning and execution. That’s where SOC teams come in. However, not all organizations need to be expert in cybersecurity, what they actually need is to acknowledge the possible threat and the will to deal with it. There are organizations who have experience in using state-of-the-art technology to deal with current and future threats. A quick audit of current systems, followed by a detailed action planning will be the right place to start to secure your healthcare systems from potential hackers.