As our IT infrastructures become more and more advanced in this era of IoT devices, public cloud applications, and billions of mobile users, malware and hacker attacks are also becoming increasingly sophisticated. With information and valuable data spread out on the cloud, the traditional castle-and-moat approach can no longer meet the requisite standards of IT network security.
In this approach, the IT infrastructure is secured by making it harder for anyone outside the network to get in. However, those already inside a network have uninhibited access. With sophisticated tech-tools at the attackers’ disposal, these security walls are no longer impregnable. Once access is secured, attackers get a free reign over the entire network.
The fact that data is no longer stored in just one place makes the castle-and-moat security more vulnerable and less effective. In light of the changing dynamics of the IT world, building cybersecurity systems equipped to protect tech infrastructure and data from all types of threats has emerged as a pressing need.
Zero Trust Architecture has emerged as an answer to these changing IT security requirements and is fast becoming a new reality for organizations across the board. What is Zero Trust Architecture and how does it cater to your cybersecurity needs? Let’s take a look:
What is Zero Trust Architecture?
The entire concept of Zero Trust Architecture is summed up in its name – it’s an architecture that operates on the ‘nothing can be trusted’ paradigm. The concept was floated more than a decade ago by John Kindervag during his time as an analyst with Forrester Research and finds itself becoming more and more relevant as organizations strive to beat cybercriminals to the punch.
Under the Zero Trust philosophy, no user, device, or application trying to interact with the architecture is considered secure. On the contrary, the basic premise is to treat everything as a potential threat and grant access only after verification. The Zero Trust Architecture operates without any trusted perimeter that mandates strict verification for any and every device and user accessing resources on a private network.
The approach to cybersecurity is not rooted in any one specific technology. Instead, it relies on a mix of technologies and principles to provide holistic network security that underlines the following paradigms:
The Never Trust, Always Verify Principle
Conventional security models operated on the assumption that all activities being carried out inside a cyber network were secure and trustworthy. However, this traditional approach has not been able to weed out modern cyber attacks as well as insider threats. That’s where the ‘never trust, always verify’ principle of the Zero Trust Architecture comes into play to plug the gaps.
This is achieved by adopting measures such as applying user context, providing enhanced visibility for internal traffic, and putting in place next-gen firewalls equipped with decryption capabilities. Zero Trust is determined by leveraging granular perimeters enforcement and micro-segmentation, based on variables such as user, data, and location.
As a result, Zero Trust Architecture does not allow threats that have impeached a network to go undetected, move around freely or morph, steal or destroy valuable business data.
A Counter for Later Threat Movement
The key objective of Zero Trust Architecture to counter lateral threat movement inside a network. Lateral movement refers to different tools and techniques used by attackers to navigate through a network in search of valuable data and assets. This becomes crucial as the point of infiltration into a network is seldom the attackers’ target.
For instance, an attacker who gets into a private network through an endpoint would need to move laterally within the environment to reach the data centers they want to target. Zero Trust Architecture can prevent this by tracking the movement of a user when an anomaly is detected and blocking it.
What makes this system nuanced is that the movement and access can be defined as per logical or pre-appropriated interactions with a network. For example, members of the marketing team accessing sensitive financial files can be defined as an anomaly whereas the same users can be granted unbridled access to marketing content, assets, and CRM data.
Components of Zero Trust Architecture
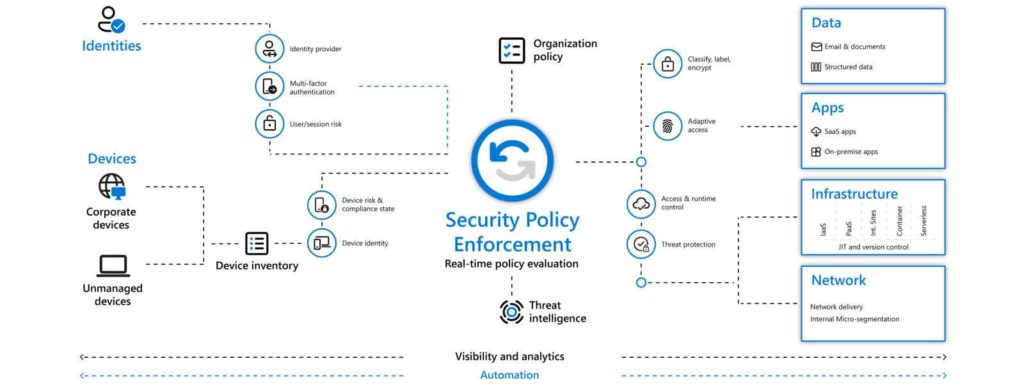
Rather than assuming that everything protected by a firewall is safe, Zero Trust Architecture verifies, authenticates, and encrypts every request before granting access. It relies on the following components to detect and address anomalies in real-time:
- Identities: The architecture relies on strong authentication methods to verify and secure every identity within a digital estate.
- Devices: It ensures compliance and health of every device by gaining visibility into it before granting access to the network.
- Applications: Zero Trust Architecture relies on real-time analytics to monitor and control user actions. This enables it to discover shadow IT and ensure that gate access and in-app permissions are granted only to legitimate applications.
- Data: The system is characterized by a shift from perimeter-based protection to a data-driven approach. Its rich intelligence facilitates the classification and labeling of data, thus, allowing encryption and restriction of access in line with pre-defined organizational policies.
- Infrastructure: It protects the infrastructure by using telemetry to detect anomalies and cyberattacks, in turn, automatically blocking as well as flagging suspicious activities by putting in place the principles of least privilege access.
- Network: All internal communications on Zero Trust Architecture are encrypted in line with its basic premise that just because a user or device is in the internal network doesn’t mean it can be trusted. In addition, it offers an added layer of security to the network through micro-segmentation, limited access, and real-time detection of threats.
How to Develop Zero Trust Architecture?
Adopting Zero Trust Architecture means consciously investing in a strategic initiative that can prevent data breaches by eliminating the element of trust from the network architecture of an organization. While it is without a doubt a more holistic approach to cybersecurity capable of protecting operations from sophisticated cyberattacks, many organizations are still wary of adopting it owing to the perception that it is a costly and complex affair.
However, this perception couldn’t be farther from the truth. Zero Trust system can be built using the existing architecture and does not entail a rip and replace approach. That’s because you don’t need any specific Zero Trust products and tools to institutionalize this system. Your existing cybersecurity setup may already have products that work seamlessly with a Zero Trust environment, and some that don’t.
Making the shift from a conventional cybersecurity setup to a Zero Trust environment simply entails leveraging the ones that do, looping out the ones that don’t, and if necessary, supplementing the existing infrastructure with additional tools and resources. This is what makes this cybersecurity approach easy to develop, deploy, implement and maintain.
You can develop a Zero Trust Architecture in your organization in four simple steps:
- Zero-in on the Right Products: Zero Trust needs traffic context and visibility to work optimally. For that to happen, you need a next-generation firewall with decryption capabilities through which the traffic can run. This firewall protection also acts as ‘border control’ within the network, enabling micro-segmentation.
- Monitor and Verify Traffic: The Zero Trust Architecture also mandates the ability to track and verify traffic moving back and forth between different operational areas within a network. This is imperative for the ability to track lateral movements and spot anomalies and threats.
- Two-Factor Authentication: Your Zero Trust Architecture must also comprise two-factor authentication, supported by other verification processes such as biometric scans, to enhance authentication abilities – and by extension, make networks more secure.
- Implement a Zero Trust Approach: Once all the cornerstones of the system are in place, it is time to implement the Zero Trust approach to your operations. This is what will ultimately help you identify business processes, data, users, data flow, and flag associated risks – both real and potential. It is also imperative for institutionalizing policy rules and criteria for flagging and responding to threats. These rules can, then, be updated automatically depending on the extent and nature of associated risks with every iteration.
How to Make Zero Trust Work?
The fundamental ethos of which Zero Trust operates can sound somewhat intimidating – ‘trust no one’. However, if you look at it practically, it is akin to setting up several check posts within your network, so that no unauthorized entity ventures where it shouldn’t. To make it work in true earnest, organizations adopting Zero Trust Architecture must continually commit to verifying and validating permissions and rights before granting access to any area or asset within their network.
One simple example of this would be that simply validating an account by entering a username and password doesn’t imply that the entire network would treat that user as ‘trusted’. With effective Zero Trust in place, your IT network will grant access to the said user only to those areas for which permissions have been specifically granted.
The security tools within the Zero Trust Architecture will track the user’s behavior at all times, flag it, and raise an alert as soon as they attempt to access something that’s outside the purview of their permitted areas.
For this approach to work effectively, your Zero Trust system must focus on five key elements – user trust, device trust, application trust, transport trust, and data trust. So far, most Zero Trust systems focus heavily on the first two – user trust and device trust. While that is understandable since cybersecurity has traditionally been tied to validating user-related factors, in this dynamic era, the scope has to be widened beyond the identity standpoint.
The aspects of application trust and data trust are equally important – if not more – for the success of an organization’s Zero Trust cybersecurity programs. Even more so when you’re looking to apply this principle across the board of cybersecurity.
To make that happen in a way that helps your leverage Zero Trust Architecture optimally, first and foremost, you need to approach it in a way that controlling access does not impact the business operations negatively. A robust zero-trust environment is one where access to every user is limited and controlled but in a way that doesn’t impede the smooth running of everyday operations.
A data-trust lens can be a crucial piece of the puzzle in making that happen. Rather than giving unchecked access to validated users in a certain area or withholding access from specific areas, you can hide specific data and files from those without authorization to access them. This can act as an added layer of protection that secures data beyond just identity-level permissions, without in any way impacting the movability of authorized users.
These hidden objects – be it folders, files, cloud shares, or mapped networks – remain unavailable to cybercriminals, as they have no way to access the data they seek. Thus, protecting organizations against ransomware and data theft attacks.
Similarly, application trust also takes the security layers of the Zero Trust environment beyond user privileges. In this case, granting access is not just subject to whether a query is authorized but also whether the application making that query can be verified and validated.
This can prove especially beneficial in preventing unauthorized access from dubious applications that your regular users aren’t likely to use for accessing data. This is also the most potent element of Zero Trust Architecture in spotting, flagging, and deflecting attacks from cybercriminals probing open services and ports to compromise and breach the security firewall. Application trust not only helps in swatting attacks but also proves instrumental in steering such elements into a decoy environment where adversary intelligence on them can be gathered.
Conclusion
Any futuristic organization that operates in a next-gen tech environment can benefit from the Zero Trust Architecture that can safeguard against complex cyber attacks capable of costing businesses millions of dollars. In the modern digital world, the perimeter-based approach to cybersecurity is often found lagging to counter and thwart complex threats floating around in the cyber world. Zero Trust Architecture has been designed to cater to the realities of this very landscape.
