Why Container Security?
The domain of modern software development always remains subject to the pushes and pulls of evolution. One of the primary imperatives in custom software development concerns the creation and deployment of agile practices, primarily because these serve to boost the speed of software operations. In this context, container technology has emerged as the preferred means to package and deploy applications.
However, specific challenges persist in terms of building and maintaining container security. Some of these challenges stem from arcane security policies and checklists that do not consider containers being used in an organization or an enterprise. The situation can be addressed through the creation of additional (and updated) security policies, the building of runtime tools, the decoupling of services, and putting in place efforts that balance the networking and governance needs of containers.
What is Container Security?
Container security primarily denotes the practices that protect the integrity of containers. The term also implies actions that secure the container pipeline and the application, ensure the container deployment environment and infrastructure, activities that integrate repositories with widely used enterprise security tools, and the enhancement of current policies that govern digital security. Therefore, container security needs to be integrated and must remain continuous at all times.
- Software developers and architects must ideally begin with finding trusted sources for base images. These base images are the starting point that helps to create derivative images.
- In line with this, developers and architects must adopt a layered security strategy that can defend containers from a range of risks. These include ransomware, compromised containers, distributed denial of service attacks engineered at the application level, cross-site scripting attacks, etc.
Do you really have to worry about Container Security?
New types of threats are emerging in the domain of new container security. Some aspects of such risks are amplified because running containers in a large-scale production environment in itself pose significant threats to an application in the event of a breach.
Attackers are continually scanning for vulnerable points; these include container run time images, image registries, and many of the tools deployed to manage a modern containerized environment. Additionally, the runs vulnerability (announced recently) poses the most significant security vulnerability in terms of its implications for production environments.
Security experts note, “The vulnerability allows a malicious container to (with minimal user interaction) overwrite the host runC binary and thus gain root-level code execution on the host. The level of user interaction can run any command (it doesn’t matter if the command is not attacker-controlled) as root within a container.”
Further, according to Rami Sass, the CEO of WhiteSource, hackers can exploit known vulnerabilities in container host systems. This makes it possible for a hacker to use not just one particular container, but any of the thousands of bottles within any of the other impacted systems. This scenario makes it crucial for any company running containers to patch runs immediately, using competent solutions that address these security concerns.
In recent times, the developer community and security researchers have realized the importance of hardening an application build and deploying workflows. Such actions can prevent attackers from accessing easy leads to exploiting the used containers.
In line with this, they recommend organizations should deploy only those container images that have undergone defined compliance checks into a production environment. Security researchers recommend that privileged containers merit particular observation because of these, when compromised, can collapse an entire container cluster.
Keeping up with the pace of Container Security
The digital security industry is designing and bringing to market critical new tools that will boost container security and provide much deeper visibility into a cloud-native computing environment.
A key challenge in cyber-security manifests in the fact most organizations have adopted containers, but a majority remains behind the curve in terms of taking best DevSecOps processes that ensure foolproof cyber-security. This flaw is widening the gap that may facilitate hacking efforts designed to compromise application development efforts.
Cultural issues and turf wars that have plagued the domain of cyber-security deserve to be resolved in the higher interest of driving the evolution of container security. For instance, the relationship between developers and cybersecurity teams, traditionally fraught with strife, must move toward resolution.
We note most cybersecurity professionals continue to harbor significant trust issues with developers. However, this is set to change because developers are increasingly being held accountable for cyber-security concerns. This change in stance may presage closer ties between developers and cyber-security teams, thereby strengthening container security.

Automation in Container Security
Automation is a pervasive phenomenon that is making its presence felt in a wide range of industries, research & development activities, cyber-security, etc. Security experts aver automation should find frequent application in security testing. In such a scenario, security configurations undergo automatic creation and updates – even though applications and deployment policies undergo constant change.
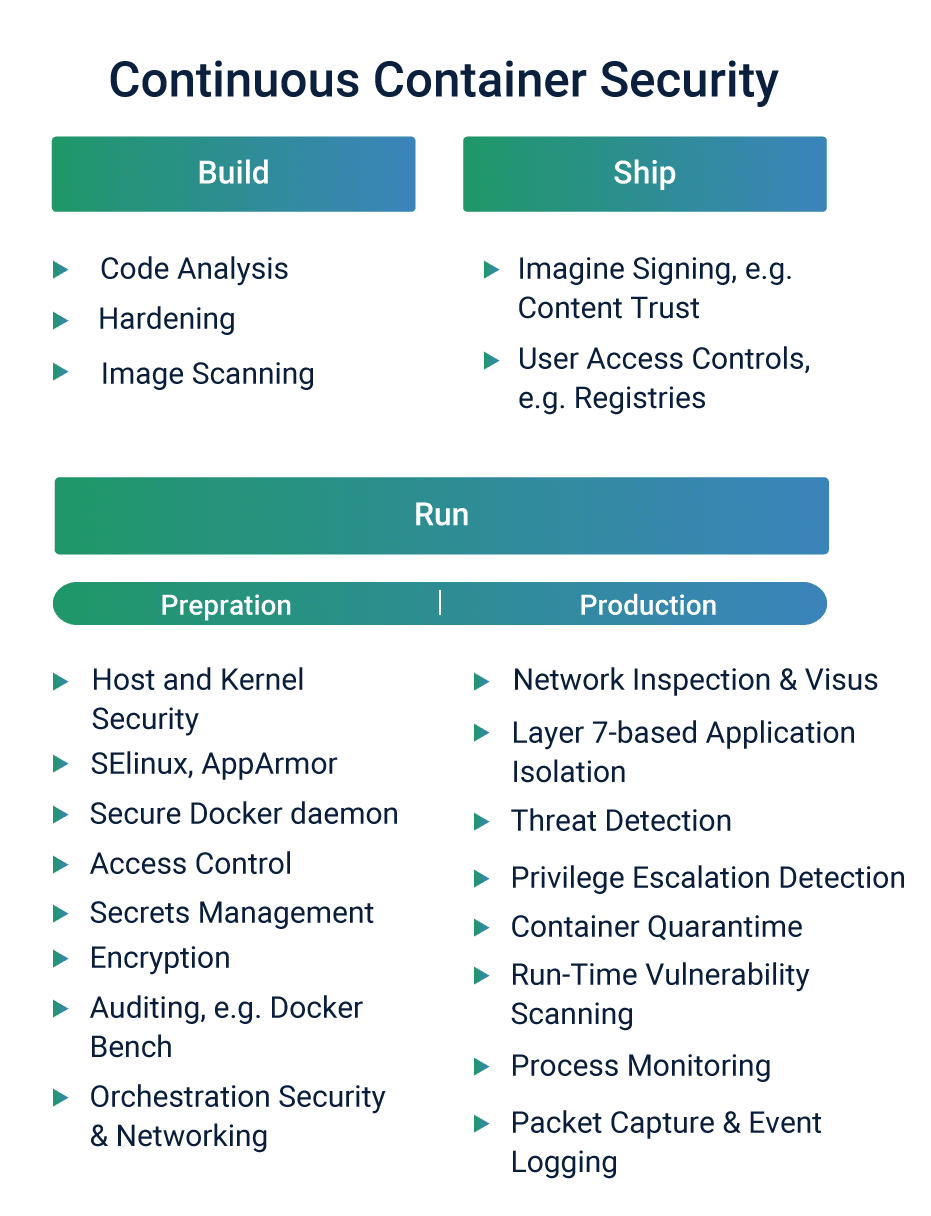
In terms of container security, automation should inform actions such as code analysis for application security flaws and image scanning for known vulnerabilities in applications and libraries.
Also, automation technologies should dominate image signing, tagging, and access controls, security testing for images, hosts, and containers. Further, automation should find a significant presence in actions pertaining to logging, packet capturing, and integration with SIEM systems, the orchestration of policies that require deployment of monitoring and security containers, host and kernel security settings when deploying new nodes, and security policy enforcement when containers scale up, down, and across applications.
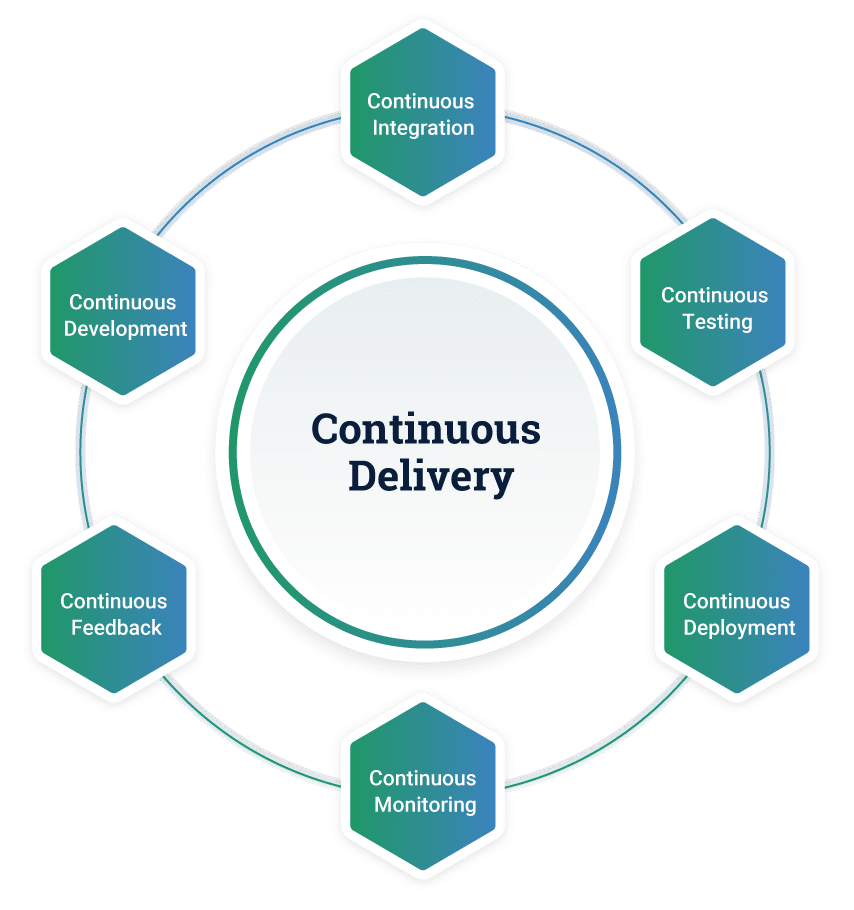
- Continuous Integration (CI)
Eternal security is one of the most favored techniques adopted by developers and architects. This approach implies that developers must gain a thorough understanding of the full spectrum of risks facing a container. After that, they must work to reduce the scope of risks within the application code. Code analysis can help achieve this, wherein developers make use of code analysis tools to recognize and report potential vulnerabilities.
Continuous security also implies hardening measures, wherein developers remove libraries and packages that are not required in a bid to reduce the attack surface offered by a container. Substantially, they are reducing the complexity in the scenario to immunize the container from attacks. Further, image scanning (and registry scanning) actions form a crucial part of the strategy to perpetuate eternal security. Such measures must be ideally enforced before the shipping phase, wherein container images are scanned for vulnerabilities that may facilitate an attack.
BENEFITS
Developers that favor continuous integration (CI) practice a set of actions to achieve their aims. They typically merge their changes back to the main branch frequently in a bid to dodge the (considerable) problems that arise from integration efforts hastily announced on the day of release.
As part of continuous integration, their changes are validated by creating a build and executing a range of automated tests against said build. Therefore, continuous integration is powered by a great emphasis on testing automation procedures that ensure the application does not undergo stress whenever new commits are integrated into the main branch.
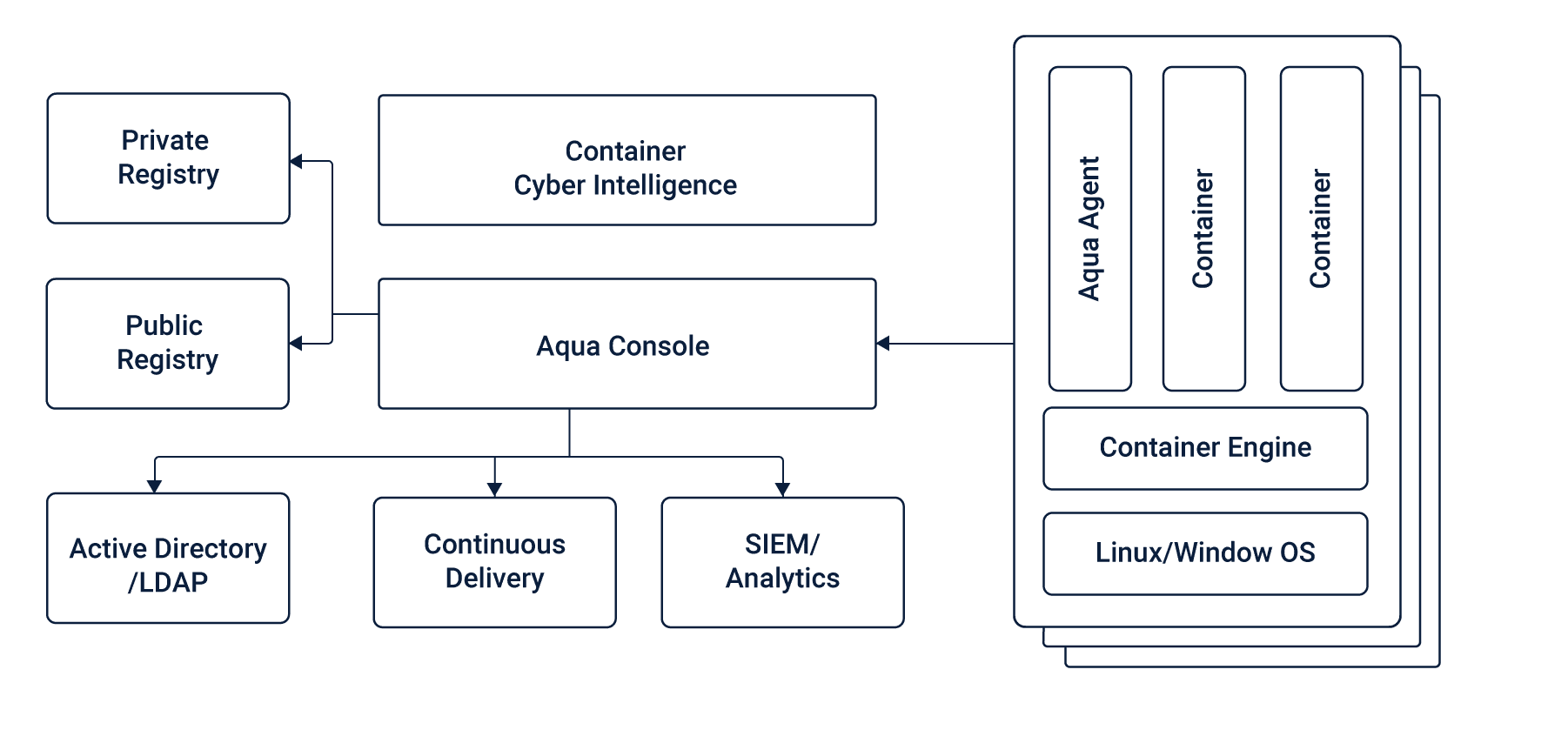
Native plugins for continuous integration tools like Jenkins are incorporated into Twistlock, as is a standalone vulnerability scanner that plugs directly into an existing build and deploys process. Also, the Twistlock product ensures that security teams can architect quality control-centric policies that ensure only remediated images progress down the pipeline.
Meanwhile, continuous integration (CI) technologies are increasingly driving a hard focus on security. This is an outcome of the higher levels of automation and faster pace that attends modern application delivery paradigms.
Modern layered security includes real-time, run-time detection of threats and violations in response to mandates that all traffic that operates between containers must be secured. This is a tall order since containers can always be starting, stopping, and moving between hosts. Security researchers, on their part, aver security technology will require more application intelligence to be built-in because the onus for ensuring container security is undergoing a shift to DevOps services and development teams.
- Continuous Delivery (CD)
In a concerted bid to connect tool makers of continuous integration and continuous delivery packages, the Linux Foundation has sought to promote the use of open source projects to establish technical specs for continuous delivery. This is in response to the widespread adoption of continuous delivery systems driven by the imperative to shorten software development cycles. The benefit of this stance is demonstrated by the fact that software can be sent to production at any time.
The Linux Foundation has formed the Continuous Delivery Foundation with clients that include Alibaba, Autodesk, Capital One, CircleCI, CloudBees, GitLab, Google, Huawei, IBM, JFrog, Netflix, Puppet, Red Hat, and SAP.
BENEFITS
Continuous delivery systems hinge on speed – this means, as soon as a feature is ready (which means it has been implemented, code-reviewed, and tested), it is deployed to production.
In terms of business benefits, continuous delivery systems allow organizations to respond more quickly to market conditions and the evolving requirements of customers.
Continuous delivery systems ensure software releases occur at regular intervals in predictable cycles. This stance removes the pressure of orchestrating big dramatic releases and the subsequent (panicked) remediation of serious bugs – scenarios that spell disaster for IT operations teams, software development groups, and quality testing personnel.
Frequent feedback represents a priceless asset for modern organizations. Continuous delivery systems imply the delivery of new features to markets, thereby helping elicit constant feedback from customers. This ignites a virtuous cycle wherein feedback enables learning and informs the development of future software. Industry observers note that enlisting the help of customers also offers the latter a sense of loyalty and co-ownership. This strengthens the bonds between software makers and those that use their products.
Essentially, the continuous delivery methodology enables a proper feedback loop that serves to accelerate the resolution of issues – while these are fresh in the minds of developers. Also, tools and processes designed to enable version control help developers to keep track of the changes engineered into a project without losing sight of the objective.
Further, tools for automating the provisioning of environments help to save time and efforts, thus driving compliance and ensuring security best practices from the beginning of the development lifecycle. Bugs (glitches in software) continue to represent an ever-present threat to the performance of software products. Continuous delivery systems reduce the impact of bugs by delivering software in small batches. In case bugs are detected in a batch, software developers have to run through fewer volumes of code to identify and remediate the glitch. Thus, bug hunting and remediation consumes fewer resources and poses less of a headache for software architects and the developer community.
What should you be doing?
if you’re using containers you should be looking to secure it without further ado. The threats are increasing by the day and automation can be your aid to thwart attacks.
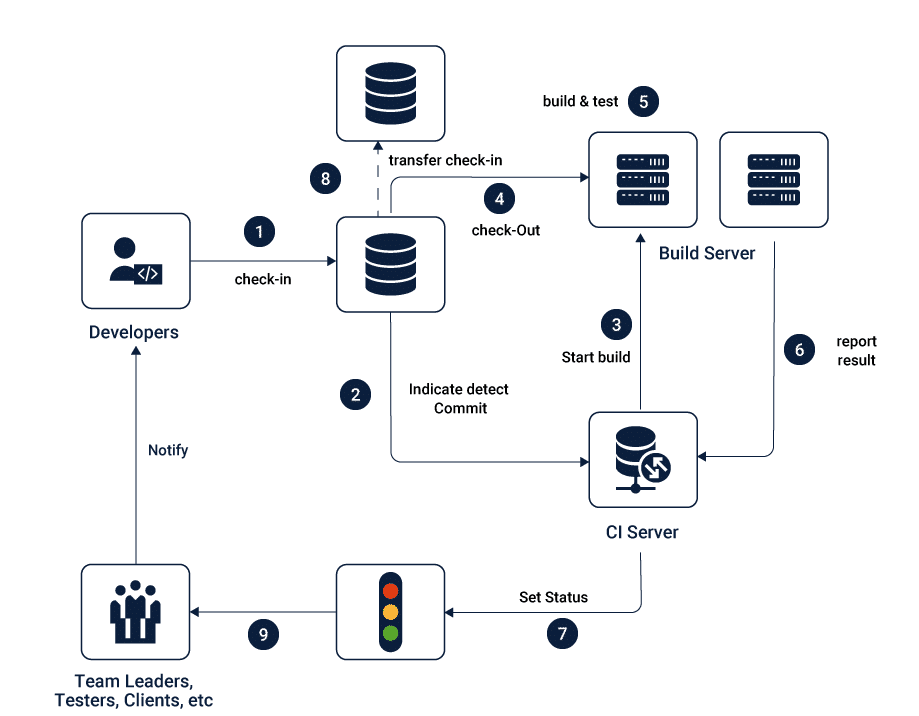
A high level container security flow can look like this –
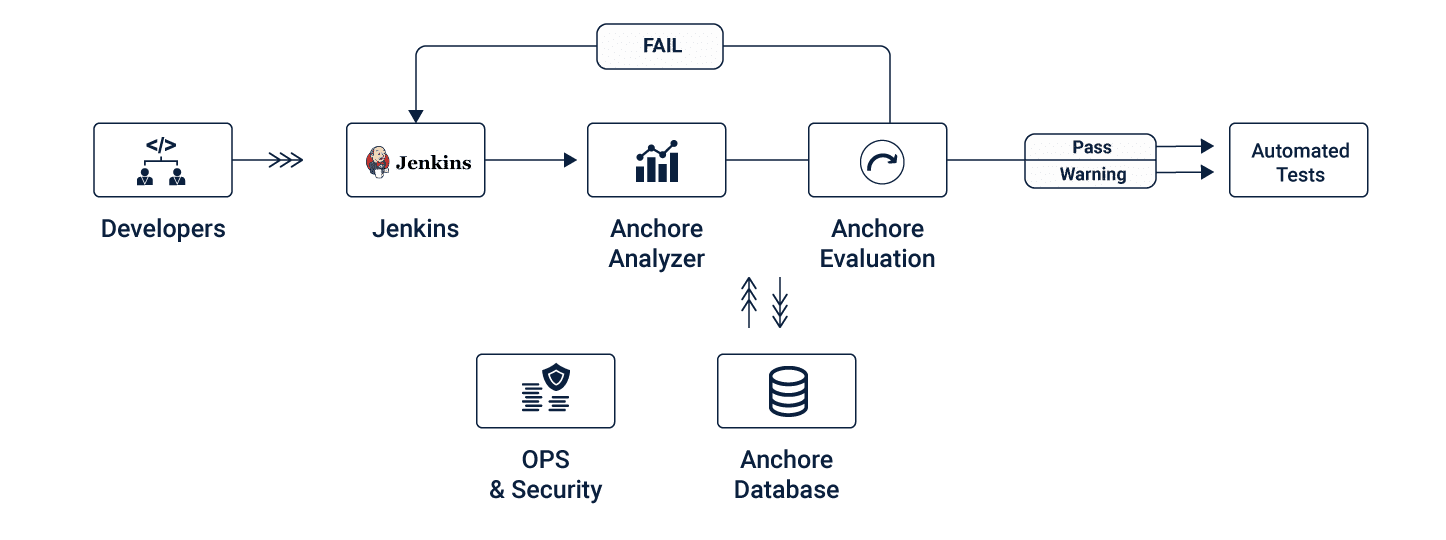
To kickstart this initiative you can align your internal teams and identify champions for security. Otherwise there are plenty of reliable and trustworthy offshore companies that have experience in this.
Once you have a team that is capable, you should be charting out Goals and identifying tools to help this initiative succeed. A well set process goes a long way to ensure the success of your project.
You can always contact us for a free consultation around this.