Introduction
A plethora of devices connected and sharing information is called the internet of things. These devices collect, send and receive data to applications, objects, and servers. They are used in various industries like automotive, industrial automation, medicine, security systems, and manufacturing.
There are various protocols and standards to connect. To decide a protocol, we need to consider the following aspects:
- bandwidth
- range
- power consumptions
- node of the protocols.
This article is aimed at understanding IoT standards and protocols offered by Internet Engineering Task Force (IETF), Institute of Electrical and Electronics Engineers (IEEE), and the International Telecommunication Union (ITU).
The following will give the protocol structure much better:
- IoT Data Link Protocol
- IEEE 802.15.4e
- IEEE 802.11 ah
- WirelessHART
- Z-Wave
- Bluetooth Low Energy
- Zigbee Smart Energy
- DASH7
- HomePlug
- G.9959
- LTE-A
- LoRaWAN
- Weightless
- DECT/ULE
- Network Layer
- Routing Protocols
- RPL
- CORPL
- CARP
- Encapsulation Protocols
- LoWPAN
- 6TiSCH
- 6Lo
- IPv6 over G.9959
- IPv6 over Bluetooth Low Energy
- Session Layer Protocols
- MQTT
- SMQTT
- AMQP
- CoAP
- XMPP
- DDS
- IoT Management Protocol
- Interconnection of Heterogeneous Datalink
- Smart Transducer Interface
- Security in IoT Protocols
- MAC 802.15.4
- 6LoWPAN
- RPL
- Application Layer
Background of IoT Protocol
In 1982, the first machine which can communicate, and track record was created. It was a soft drink vending machine from Coca-Cola. In 1999, an RFID technology researcher, Kelvin Ashton coined the term internet of things. In two decades from 2000-2019, the system had undergone rapid development and found many practical applications.
Since then, it has evolved as a different internet world, it requires a new range of standards and protocols. Although new standards are available some applications still use technology like HTTP.
Necessity of IoT Protocols
The following points will emphasize the necessity of these communication protocols and how they help us in overcoming issues:
- Can be used to call for help in case of emergency or failure of another device which is connected.
- Assist in notifying the user about the emergency.
- Economically profitable, as the end-user data can be used to analyse trends and market.
- Minimizes risks of security threats.
- Unification of all the IoT communications available worldwide.
- Heterogeneity within the connected systems.
Types of IoT Connections
The connections of the devices in IoT platform can be of following types:
- Device to Device (D2D)
- Device to Gateway
- Gateway to Data systems
- Between data systems
Let’s discuss in brief about each connection type of IoT.
- Device to Device (D2D): It is the type of communication in which two IoT devices communicate. Example: the communication established between a smartphone and the smartwatch. This type of connection is not very common, as many such devices couldn’t handle data from another device.
- Device to Gateway: It is the communication established between the sensors and the gateways. Such connections perform two major types of functions:
- to consolidate and route the data from the sensors to the systems
- to analyse and send back the erroneous data to the device.
- Gateway to Data systems: It is the connection established between the data systems and the gateways. Gateways are a more complex computing system to find the right protocol as they help in analysing the data traffic in the system.
- Between data systems: This is the information transfer within the cloud or the data centre. The protocols employed for such functions should be capable of integrating with existing applications, should be available all the time, should have the capacity and reliability for recovery of the data in case of an emergency.
Choosing an IoT Protocol for your communication system
Various factors must be considered before choosing a system. Most of these factors depends largely on the application but some common ones have been discussed here:
- Number of connected devices
- Reliability of the network
- Delays while transmitting real-time data
- Security of the network
- Cost of infrastructure and connection
- Handling of multiple heterogeneous devices
- Application configuration
- Traffic management
The range decreases as the bandwidth increases. LoraWAN is the only long transmission that can be used. The 3G, 4G and 5G network for the medium distance transmission. The rest of all protocols are used for short-range transmission.
Types of IoT Networks
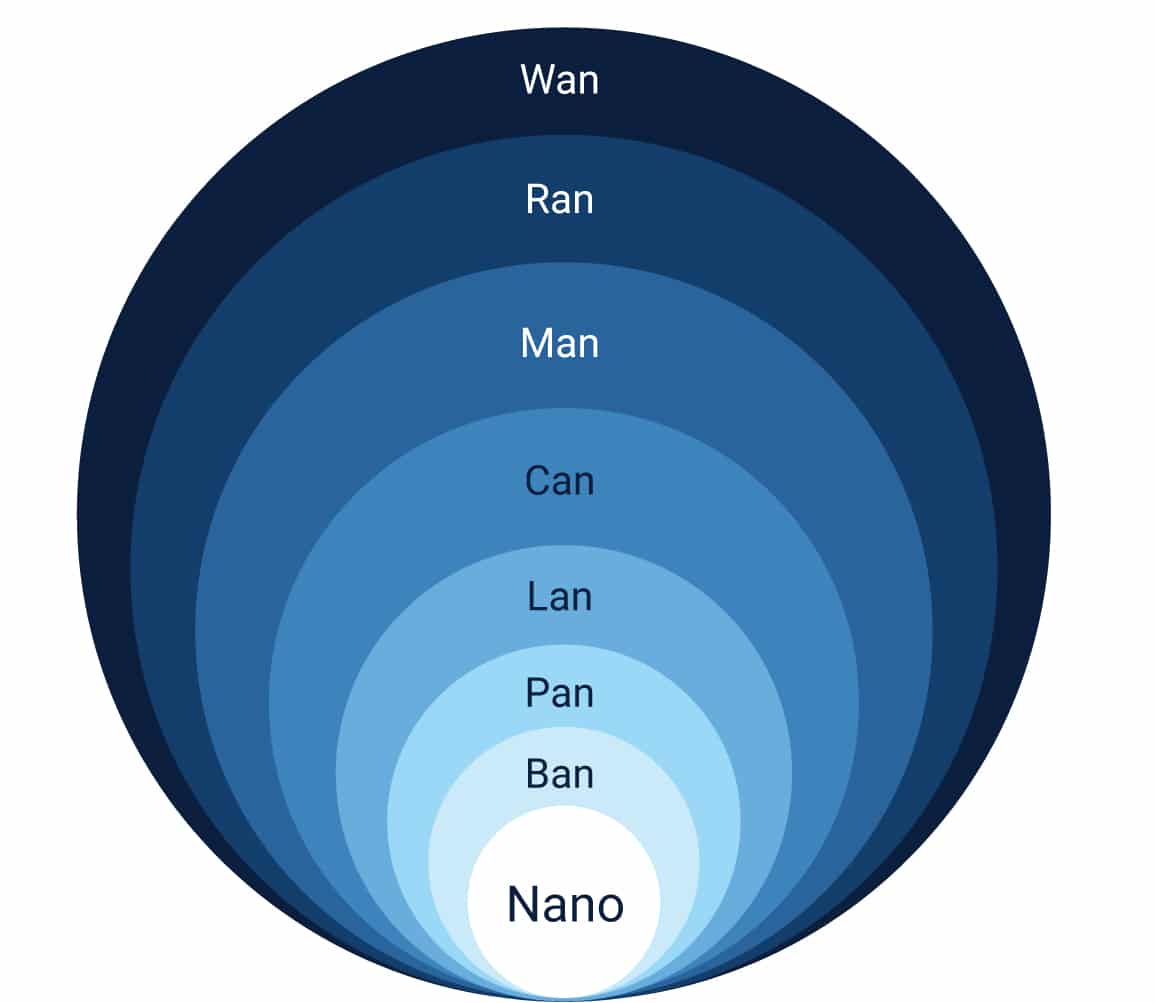
- Nano network: A few or a small number of devices connected for sensing the data, computing the data, storing the data, and actuating the response.
For example, military, biomedical, nanotechnology, etc.
- NFC (Near-Field Communication): It is for objects that are very close to each other, say 4 cm of distance.
For example, payment systems, key cards, and ID cards
- BAN (Body Area Network): Systems that are on the body, near the body or inside the body (embedded implants) are called BAN.
For example, biomedical implants
- PAN (Personal Area Network): For communication in a small range, homes with rooms like 15-20 feet apart.
For example, Virtual assistant and home security systems.
- LAN (Local Area Network): A local-area network (LAN) is a computer network that spans a relatively small area. Most often, a LAN is confined to a single room, building or group of buildings, however, one LAN can be connected to other LANs over any distance via telephone lines and radio waves.
- CAN (Campus/Corporate area network): A Controller Area Network (CAN) bus is a communication system made for vehicle intercommunication.
- MAN (Metropolitan Area of Network): A metropolitan area network is a computer network that interconnects users with computer resources in a geographic region of the size of a metropolitan area.
- WAN (Wide area network): A WAN (wide area network) is a communications network that spans a large geographic area such as across cities, states, or countries.
There are other networks also which are combinations of two or more connections between nodes such as line, ring, star, mesh, fully connected, tree, bus.
The following sections will discuss more about the protocols and standards of IoT.
IoT Protocols
Gartner in Hype Cycle for IoT Standards and Protocols has prioritized few protocols based on their project interoperability, longevity, and on maturity
levels mentioned as below:
1) On the Rise
- Backscatter Communications
- Micro OS
- Li-Fi
- 5G mMTC
- 802.11ax
- Ultrasound
- OMA SpecWorks LightweightM2M
- Hardware Security
2) At the Peak
- RISC-V
- Constrained Application Protocol
- 802.11ai
- Bluetooth 5
- FIDO Authentication Protocols
- Secure Processing Unit
- Advanced Development Boards
- e-SIM
- LoRa
- NB-IoT
3) Sliding into the Trough
- Arduino
- Data Distribution Service
- LPWA
- Sigfox
- Thread
- oneM2M
- 802.11ad
- DotDot
- MicroPython
- Bluetooth Beacons
- Wi-SUN
- 802.11ah
- 802.11p
- Trusted Environments
- LTE-M
4) Climbing the Slope
- Message Queue Telemetry Transport
- IPv6
- AMQP
- 6LoWPAN
5) Entering the Plateau
- SCOTA
Data Protocols
Whenever we have a need to transfer the data from our system to an IoT platform or any other system which is connected, we require a data protocol. The following are the three main types of data protocols:
- a) Message Queuing Telemetry Transport (MQTT)
- b) Constrained Application Protocol (CoAP)
- c) Extensible Message and Presence Protocol (XMPP).
Here we will be discussing some major data protocols:
- IEEE 802.15.4: It supports slow power communication. This protocol is famous for the Medium Access Control (MAC) layer. In specific it talks about the following MAC feature like:
- Slot frame Structure
- Scheduling
- Synchronization
- Channel Hopping
- Network formation
- IEEE 802.11 AH: It is an extension of the original version IEEE 802.11. It is designed standard for low overhead and power-friendly communication that is suitable for sensors and nodes. It includes features like:
- Synchronization Frame
- Efficient Bidirectional Packet Exchange
- Short Mac Frame
- Null Data Packet
- Increase Sleep Time
Let’s discuss each of the above mentioned data protocols in brief:
Constrained Application Protocol (CoAP)
It was designed in 2013 to transfer the HTTP model into a usable protocol that can be used in restrictive environments of device and network. The CoAP is based on User Datagram Protocol (UDP) to establish secure communication between endpoints. The following are the features of CoAP:
- Open IETF Standard
- Compact 4-byte header
- UDP, SMS and TCP support
- Strong DTLS security
- Asynchronous subscription
- Built-in discovery
It avoids ambiguity through the following strategies
- HTTP get
- put up
- delete
- placed strategies
It uses RESTful architecture which is divided into two main layers messaging and request/response. CoAP has four messaging modes:
- confirmable,
- not confirmable
- piggyback and
- separate
Confirmable represents reliable transmission. Not conformable denotes the unreliable transmission. Piggyback is the direct communication with the client or server within acknowledgement. In the separate mode, the message is received separately from the acknowledgement.
MQTT (Message Queue Telemetry Transport)
It is a lightweight protocol that is for transmitting data from sensors and applications to middleware. Arlen Nipper (Arcom) and Andy Stanford-Clark (IBM) developed this protocol in the year 1999. The main function of this protocol is to obtain data from all the devices. The core mechanisms involve:
- Subscriber
- Publisher
- Broker
Publisher generates and transmits data to the publisher with the help of the broker. The broker ensures the security by checking and rechecking the authorization of the publisher and the subscriber. The following are the benefits of this protocol:
- cheap,
- low-power consuming devices
- small devices
- low and vulnerable bandwidth network.
- More memory sources
- Little processing
- Operation over wireless networks
- Good reliability
Modes of achieving this are called Quality of Service. The following are the QoS:
- QoS0 (At most once): Fastest but least reliable. The publication will be sent but confirmation will not be received.
- QoS1 (At least once): Fast message delivery but duplicates may be expected.
- QoS2 (Exactly once): Most reliable as the duplicates are controlled.
It acts as an embedded bridge between the application and middleware. Below described are the duties of the publisher, broker, and subscriber.
- Publisher: lightweight sensors which connect broker to send data
- Subscribers: Applications that receive sensory data and inform the broker about newly received data
- Brokers: Classify sensory data and send it to the subscribers.
Extensible Messaging and Presence Protocol (XMPP)
In 1999, Jabber open source community developed this is for real-time messaging. This is written in XML language and it is message-based middleware. It allows real-time transmission of message-based data among the clients. Since it is extensively used, lightweight XMPP for IoT applications was developed. It has some drawbacks such as the services are neither of good quality nor end-to-end encryption is offered.
DDS (Data Distribution Service)
It was developed by the Object Management Group (OMG) which can be deployed in the low footprint devices and also in the cloud. It offers various quality services like
- a) security
- b) urgency
- c) priority
- d) durability
- e) reliability
It has two main layers namely:
- Data-centric publish-subscribe: It delivers the information to subscribers. It ensures that the data which is distributed is resource-aware, scalable, and efficient.
- Data-local reconstruction sublayers: It provides an interface to DCPS functionalities.
Examples of the applications of this protocol are:
- Air-traffic system control,
- Smart grid management,
- Autonomous vehicles,
- Transportation systems,
- Robotics,
- Power generation
- Healthcare services
It is applied in all places where large lightweight systems are interconnected to send and receive data from the cloud.
Advanced Message Queuing Protocol (AMQP)
It was developed in 2003. It has standard open-source subscription protocol. It is the only protocol that is useful for end-to-end application for individual IoT. It has the benefit of:
- message orientation
- queuing
- routing
- reliability
- security
It is in an application layer with international standards. It is best suited for message-based middleware environments. It comprises of following three components:
- Exchanges: gets and puts message in the queue
- Message queue: stores the message until processed
- Binding: tells the relationship between the first and the next component
Near Field Communication (NFC)
It is based on the electromagnetic induction loop between two antennas in the radio frequency which is available at ISM band of 13.56 MHz on ISO/IEC 18000-3. The frequency bands are available at a rate of 106 Kbit/s to 424 Kbit/s.
It requires an initiator and a target. The initiator generates the RF field. It has two modes of communication:
- Active communication mode: Both devices the initiator and the target communicate alternatively. Both the devices are electrically powered.
- Passive communication mode: The initiator provides a carrier field while targeting answers by modulating.
Benefits of using NFC include:
- Low-speed connection
- More capable of wireless communication
- Short-range
- Support encryption
- Less private RFID systems
- Consumes less power
- Does not require pairing
- The maximum rate of NFC is 424 Kb/s
- Works even with unpowered devices
- Compatible with existing systems
It also has a few drawbacks such as:
- Short-range is not available in many old devices
- Take time to set up
Challenges Faced by IoT
Developing such a complex IoT system is challenging. Some of the challenges faced by IoT are:
- Mobility
- Reliability
- Scalability
- Management
- Availability
- Interoperability
- Security
- Privacy
