Cloud has become the de facto norm in the tech world today. Companies that require significant computing and storage are opting to shift their services onto cloud infrastructures. Increasingly so, companies that need to ensure enhanced security are adapting their infrastructures to go the cloud-native route.
Cloud-native applications leverage the power of the cloud to implement flexible and resilient solutions that are implicitly secure.
How Does Cloud Work?
Cloud refers to the remote provision of storage, computing power, or application software. The cloud service provider maintains the underlying infrastructure.
Users can choose to go for any cloud providers from the public, private or hybrid sector, as per their requirements.
Why are Teams Increasingly Choosing Cloud?
The advantage of using cloud-native solutions is that on-premise hardware is no longer needed. This saves the company from managing the space, power, and team resources to operate this hardware efficiently. Cloud infrastructure can be operated by a relatively smaller team and can easily be scaled up or down as per demand and performance needs.
The Reason Security Needs to be the First Priority
In recent years there have been a significant number of large-scale security breaches. Year by year, the count of security incidents is rising exponentially. The severity of these breaches is increasing as well, and large-scale digitization means that a lot of sensitive user information is at risk. The risk for identity theft could ruin a company’s reputation and leave it liable for security compliance violations.
Studies have found that factoring in reputational damage, legal liabilities, and remediation measures makes the average cost of a single data breach around $3.86 million as of 2020.
While the average time to identify a breach in 2020 was 207 days, the average lifecycle of a breach from identification to containment was 280 days.
These statistics indicate the increased need for aggressive investments in security in the cloud.
Industries that handle sensitive information, like the healthcare and finance industries, are usually the first target for hackers targeting personal data. However, smaller industries also face security threats because they are easier to break into. Security threats across technology companies are pervasive, but cloud-native security measures help to mitigate these risks.
Structure of Security Layers in Cloud-Native Applications:
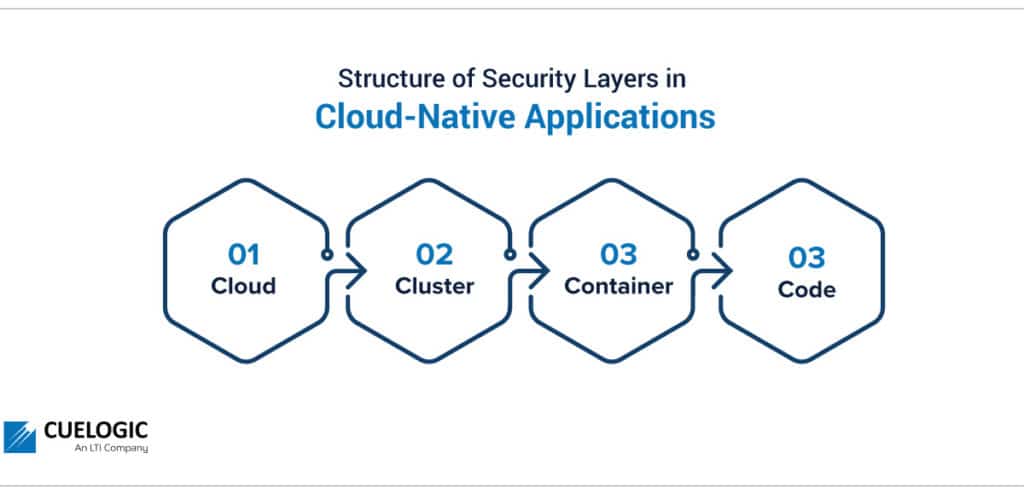
Cloud-native has described applications and services for years, but its place in security is becoming more prevalent as technology advances.
In a typical cloud-native application, there are four layers to security: Cloud, Cluster, Container, and Code. Commonly called the 4C’s of cloud-native security, this layered approach is widely recognized as the best design for securing software systems.
Cloud
The ‘cloud’ is the basis of configuring the security for an application. Each cloud provider makes recommendations for running secure workloads in their environments.
The cloud layer is the interface that interacts with the external world, which includes users, third-party plugins, and external APIs. Therefore, vulnerabilities on the cloud layer would cause a significant impact on all the services, processes, and applications that are hosted within it.
Cluster
The next layer is the ‘cluster’ layer. Applications deployed on cloud infrastructures are commonly modularised into containers and grouped into clusters. Securing a cluster involves the secure configuration of communication within the cluster and securing the software running within the cluster.
Container
Following the cluster layer in the ‘container’ security layer is the most critical part of application deployment security in cloud-native applications. Since the environment and software are packaged into containers, securing containers is unavoidable in modern cloud deployments.
Code
The final C refers to ‘code’. Developing security into an application’s code is part of ‘DevSecOps’, which involves prioritizing application security earlier in the application development lifecycle.
Benefits of Cloud-Native Security:
The benefits of going cloud-native for security are significant. The following can be considered as the main advantages of cloud-native security:
1. Security is Provided as a Completely Managed Service
Since the service provider completely manages cloud security, teams do not need to maintain resources to monitor security.
Cloud providers are expected to provide security through the entire information processing lifecycle. Cloud-native security services ensure the secure deployment of services, secure data storage with end-user privacy safeguards, secure communications between services, secure and private communication with customers over the internet, and reliable operation by the infrastructure administrators. In conventional on-premise architectures, these safeguards are the responsibility of the application teams and require the strict monitoring of applications.
2. Improved Visibility and Monitoring:
Cloud-native security allows the aggregation of information from every component of an application and provides complete end-to-end visibility about the environment. This real-time view assists in critical security-related decision-making.
Cloud-native applications also ensure easy monitoring of usage logs. By ensuring that team members have the minimum access to resources and creating dashboards for monitoring usage statistics, it is easy to understand the usage patterns. Unauthorized accesses will be blocked, and alerts can be set up to indicate such unauthorized requests.
Cloud-native security tools have evolved from providing rudimentary visualizations to sophisticated dashboards which highlight trends and can also help to predict future threats.
3. Continuous Compliance Assurance
Compliance in cloud-native applications ensures compliance with the laws and regulations that apply to the adoption of cloud infrastructures. For example, there are laws for data protection, like data localization laws and data sovereignty laws. The laws differ by country as well as by domain. Adopting a cloud infrastructure ensures compliance with these laws by default, setting a minimum standard for security measures.
4. Easily Deployable Security Architecture Changes
Rapid deployments are integral to cloud-native applications. This helps teams to apply security fixes easily across multiple environments. Infrastructures need to be kept updated with the latest security measures to combat evolving threats. Outdated software can have critical implications. An example is the Wannacry ransomware attack in 2017, which impacted around 2,30,000 computers globally. Microsoft had released a security patch that would protect Windows systems against the attack two months before the attack occurred. However, systems that had not been updated were left vulnerable. This led to a global loss estimated to be around 4 billion dollars.
5. Reliable Backup and Recovery for Data and Services
One of the most significant advantages of cloud-native applications is the ensured data backup by cloud providers. Different application tiers can set up appropriate levels of data backups. For services, critical applications can be backed up to ensure negligible downtime, with service levels agreements agreed upon as per the domain. In addition, data backups safeguard companies against system failures, data breaches as well as natural disasters.
6. Secure Infrastructure
Cloud infrastructures commonly follow a protocol to ensure the infrastructure is secured. Cloud providers maintain strict access control to servers, with only authorized personnel allowed within data center premises. They ensure strict logging or access to the infrastructure. Cloud providers invest significantly in maintaining the security of their hardware.
7. Network Security
Cloud-native deployments ensure network security controls like configurable firewall rules and continuous network traffic monitoring for reporting. The network traffic within the application components and accesses to and from the application itself are all logged for review.
Security services then ingest logs of traffic flow from applications and develop a deep understanding of usage for analyzing and predicting network threats.
8. Data Security
Adopting cloud infrastructures ensures data is encrypted at rest and in transit. Cloud-native security employs powerful key-based encryption algorithms that prevent external users from intercepting data streams as they travel to and from the cloud or accessing data files when they are saved to cloud storage. Furthermore, by identifying sensitive data, access can easily be restricted only to authorized users. These enhancements in data security have led to highly data-sensitive industries like banking also adopting cloud for their data.
9. Platform Flexibility
By supporting applications across multi-cloud and hybrid deployment environments, cloud-native security allows platform-agnostic development.
10. Automatic Threat Detection using Machine Learning Algorithms
By adopting machine learning algorithms into workflows, the identification and remediation of threats have been simplified. Automated solutions leverage dynamic analysis tools and mine historical breach information to detect cybercrimes and alert the relevant teams preemptively.
In case of a breach, event-driven automation can help to remediate and secure the application in near real-time.
11. Vulnerability Management
Cloud-native security solutions allow teams to accurately and efficiently scan for vulnerabilities everywhere within the application’s infrastructure. In addition, it helps teams prioritize between different potential vulnerabilities by identifying the highest business risks using trend analysis and threat predictions.
Use Cases for Cloud-Native Security
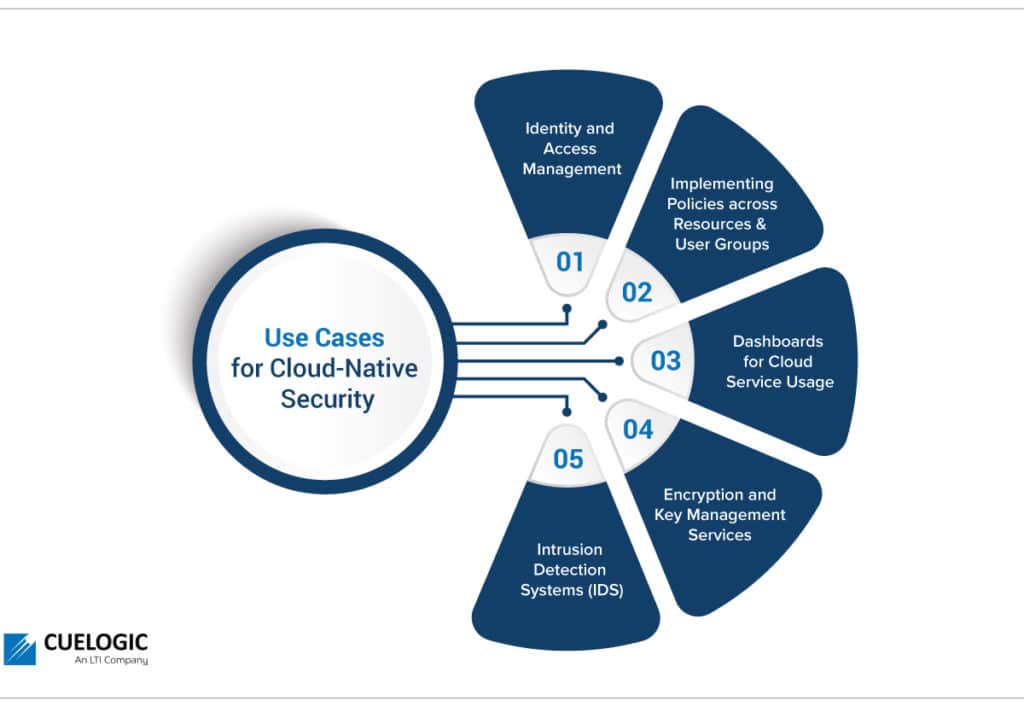
Since cloud-native security can be interpreted and implemented in different ways across domains, there are a few specific use cases that can be used across domains:
1. Identity and Access Management
IAM is a cloud service to manage the permissions for users who need to access resources. IAM policies are sets of permission that can be defined for either users or cloud resources to authorize what is accessible and what actions can be taken on the resources. Access levels can be of different types, for instance, ‘read only’ or ‘admin’ access.
2. Implementing Policies across Resources and User Groups
Cloud policies define the guidelines under which companies operate. They help to ensure the integrity and privacy of data and operations in the cloud. To maintain effective security, companies need to audit all applied policies periodically.
3. Dashboards for Cloud Service Usage
Security teams need a consolidated usage of services, unauthorized requests, and application performance. Cloud providers include dashboards with granular measurements down to the smallest workload.
Cloud monitoring dashboards have thus become compelling from a security point of view. They also enable better visibility and more informed decision-making and help meet operational targets, such as availability, performance, and budget.
Lastly, cloud monitoring dashboards provide information to security teams that would not be visible otherwise. For example, the information of when a business or technical team started using a new cloud service can indicate the start of an unexpected event. The security team can preemptively be notified about actions that may require additional monitoring.
4. Encryption and Key Management Services
Cloud deployment patterns are designed to integrate with encryption by key management. These encryption mechanisms are integrated into cloud storage services and development and deployment pipelines. This ensures development teams can easily secure their services.
5. Intrusion Detection Systems (IDS)
IDS systems help to detect network-based threats such as malware, spyware, and command-and-control attacks. IDS helps to protect systems at the cloud as well at application levels.
Best Practises for Secure Cloud-Native Apps:
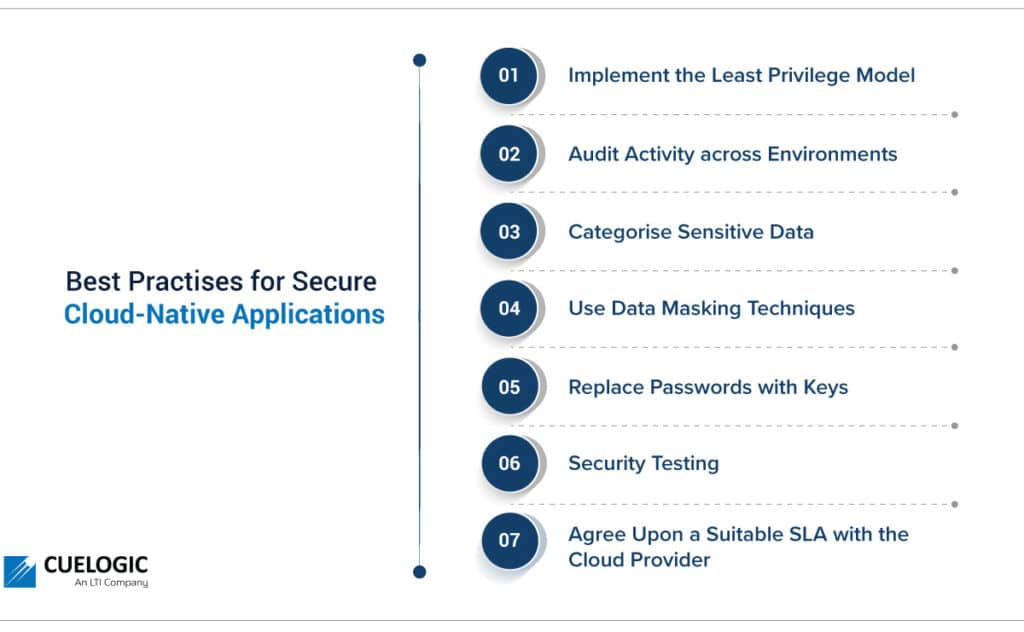
Certain standards are followed across industries to ensure that security standards are maintained in cloud-native applications. They are:
1. Implement the Least Privilege Model
By ensuring teams have the minimum access required to perform their roles, the application is safeguarded against unintended actions. This model also states that access must be granted only for the minimum amount of time required. Since most cybersecurity threats are caused due to human error, implementing the least privilege model is an effective way to enhance the security of an application. It also protects organizations from insider threat risk and is required as a regulatory prerequisite in several regions.
2. Audit Activity across Environments
Since cloud platforms can maintain logs of every administrative action and resource access, it is a standard to regularly audit activities across the cloud environments. This helps detect threatening patterns before any negative incident occurs. Log audits are also often required by regulatory compliance entities.
Apart from activity log audits, teams need to ensure that the cloud vendor also adheres to required system security audits.
3. Categorise Sensitive Data
By categorizing data as per its sensitivity, different policies can be applied across the organization’s resources. This ensures easy restriction of access. Only user groups with elevated authorities can access highly sensitive data.
4. Use Data Masking Techniques
Once data is classified, teams can choose the most appropriate masking algorithms to ensure the data is safe. Data masking is a way of converting organizational data into a fake, but realistic representation of the data figures. The aim is to protect sensitive data while providing a functional alternative when real data is not needed – for example, software testing.
Data masking changes the values of the data while maintaining the same format. The masked data cannot be reverse-engineered or deciphered. There are multiple techniques to mask data, like shuffling the characters in words and substituting characters with other characters.
5. Replace Passwords with Keys
Passwords can be considered a liability as they can be insecure and bear the possibility of being forgotten. Therefore, organisations should make public key infrastructure (PKI) part of their cloud security policies. PKI employs the use of a public and private key to verify the identity of a user before the user’s session is begun. PKI also prevents the success of brute force login attacks.
6. Security Testing
Application teams conduct functional testing with every deployment. However, security testing is equally critical, and security tests should be run in each environment of an application. DevSecOps shifts security as an early priority in the development pipeline.
7. Agree Upon a Suitable SLA with the Cloud Provider
Depending upon the criticality of the business applications, teams need to determine appropriate SLAs for the different services being used across the cloud platform. This helps to guarantee required levels of reliability, availability, and responsiveness for systems and applications. SLAs specify whose responsibility it is to resolve service interruptions. They also specify penalties if predetermined service levels are not met.
How to Implement Cloud-Native Security: Build or Buy?
The decision of whether an organization should choose a vendor provider or an internal cloud security solution depends on several factors. Organizations must perform appropriate due diligence before opting for any specific security strategy.
Security solution providers have three major deployment patterns available for incorporating security practices into the organization’s workflow: cloud-native, third party, or open-source. Other factors that companies need to pay attention to include the regulations that may be applicable for the project, for instance in certain countries, banking data needs to be hosted within the company’s geographic limits, and only cloud providers with data centers within the geographic range can be considered viable. The other factors include the team’s expertise and the team’s urgency, as each security configuration is critical to the safety of the project. Based on all these factors, teams can make an appropriate decision of going for a pre-built security solution that they can configure as per their needs or building a custom solution in case of precise requirements.
Conclusion
Since the Cloud has proven itself to be the future for technology standards, teams need to upskill and adopt Cloud as soon as possible. With this adoption comes the definite need for expertise in cloud-native security. To measure an application’s success, security is just as critical as scalability and agility. The exponential growth in technological advances means that companies need to stay ahead of the curve by adopting cloud-native security solutions faster. After all, a company’s reputation lies in how secure it is.
