Technology and its very omnipresence have brought around a lot of changes in our lives which makes it exemplary and revolutionary. Even the smallest of things can now be better transpired with the help of technology. Volumes of information flow on the internet every day which makes our modus operandi easier but going there we also have various level of security threats to this information that are broadcasted on some or the other level in multiple platforms.
This information runs the threat of getting construed in a negative manner which may bring in bad experiences and consequences. Eavesdropping from suspected cybercriminals can cause havoc in your life, and better cloud & data infrastructure should be put in place to tackle this.
There have been some security patches in place for the various architectures that are being deployed nowadays to improve the protection. To talk of these kinds of protection, most of them are of the traditional types which will lack in some of the necessary firmware which is needed to tackle these kinds of malware.
Cloud-Native applications or building applications that are cloud-based and are stored in various containers is the new go-ahead for the many organizations that are there and which gives them a new level of security.
Explaining Cloud-Native Security
Conventional methods are better being given up for new ways of dealing with cloud related threats. Nowadays, applications are being built on the point of action of cloud-based services that are being provided by the various software services companies. A change in architecture in the form of Microservices are being put to work in the process of the previously used Monolithic ones.

Traditional ways of producing software services are being given up in the form of DevOps, which is a set of software development practices that enhance the delivery of services which is fast-paced and is more reliable. You can update it frequently without any much glitches. Such high-level interaction with codes to implement such methods will give rise to various levels of security threats.
These enterprises should employ security formulas in the most innovative manner which will save them from further discrepancies. These can be discussed under:
- Repair
Malware which is the primary node of security fears feed on misconfigured or unpatched software. Sometimes these misconfigured patch takes many days to get repaired ad it is occasionally difficult to ward off the problem, but with a Cloud-Native Security’s mitigation approach, the vulnerable software can be moderated as soon as any new updates are available.This lucid approach to implement security in this manner will boost the architecture which will be implemented and with further updates, it can be made more reliable.For example, in case of your Anti-virus that you use on your Desktops, you have to cater to daily updates of the Anti-virus so that it will guard you against any new kind of threat which is looming on you. It repairs any risks that it detects and makes a protective screen against the dangers that might affect you at large. - Repave
Restoring our system from advanced persistent threats can be tough and can be carried out to the very minimum to some extent. Repaving the servers and applications from a good state will help you to improve its condition and extend its lifeline. It’s preventing yourself from a known threat by using specific preventive measures.Take the example of Anti-Virus in this too, the firewalls that it creates is just like repaving the various security levels that it has for us. - Rotate
Sometimes the precautions that we take can lead to some of the other leakages which might lead to some grave consequences which we would never like to face. The information that gets leaked is known as credentials. Here, we can rotate the credentials which will make it useful for a short period.For example, using encryption for your valuable information which changes from time to time will make it hard for hackers to decode. Faster technological innovations also lead to faster implementation of architecture which can be sometimes done through a lackluster manner which makes it all the more vulnerable to discrepancies. Cloud-based services are the new cool amongst the industrial enterprises, therefore, protecting them against the large anomalies that loom because of it following the container style architecture is very important.With these 3 R’s, cloud-native security services can be approached through a more practical approach. These cloud-native security services are borrowed from the cloud-native development services of the various software services that have been implemented.
Build up a “Cloud-Native Security”
It refers to some of the essential cloud-native apps which you can deploy by building them up with basic architecture related to this. Here are some of the primary ways in which you can authorize that.
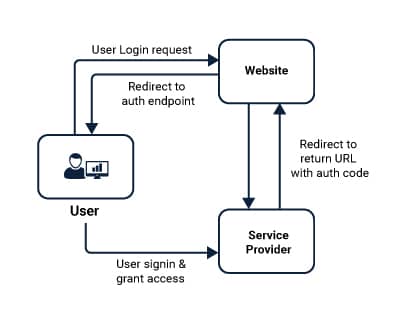
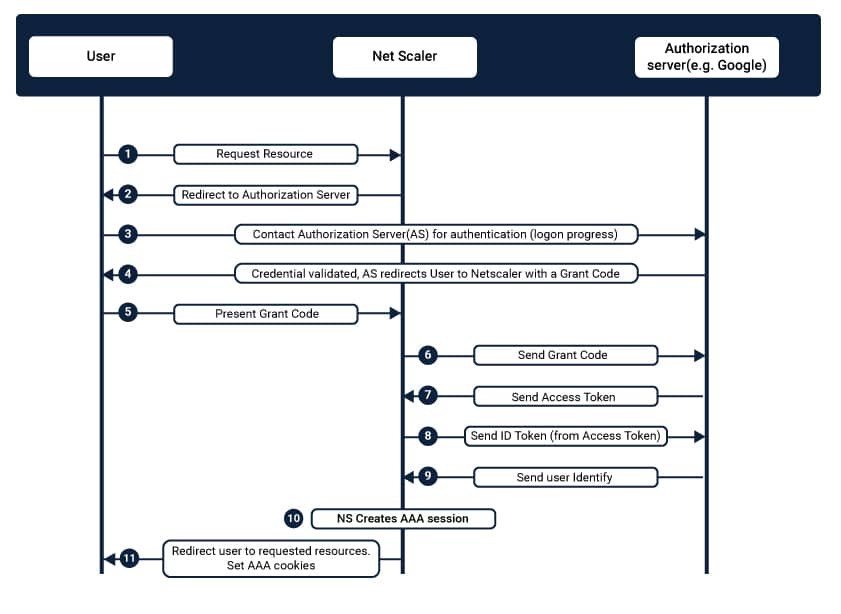
- OAuth (Open Authorization)
This framework allows an HTTP service to the third-party application via minimal service. It is either done by architecting an interaction between the resource owner and the HTTP service or by allowing the third to do that. Directly speaking, OAuth allows a user’s account information to be used by third-party applications without hampering much of the user credentials.Information from platforms such as Facebook and Instagram are given to them but which is well construed with security patches. - OpenID Connect
It is one notch above the OAuth authorization framework and is capable of giving additional authentication capabilities to provide a further protective security patch to the framework.
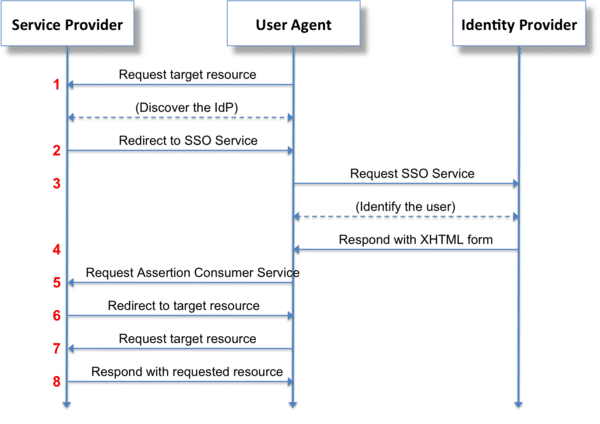
OpenID Connect also aims at reducing the complexity that is built by avoiding XML and SOAP overheads as seen in the cases related to SAML. It is authenticated by third-party services which are known as identity providers. Users get to choose their preferred OpenID providers to easily to log into the apps or systems that accept the OpenID authentication scheme. - SAML (Security Assertion Mark-up Language)
It is an XML-based open standard data format which is used for exchanging authorization and authentication data. This work is basically between a Service Provider that hosts Web Applications and an Identity Provider which maintain and provide an electronic identity for their authentication and processes. The best example for this is LinkedIn, Facebook, Google, and other such sites.The structure provides authentication and authorization processes for users over a growing world of a dynamic and static pool of platforms. It enables a better and robust platform in a cloud-native way by implementing independent roles to platforms of web applications. It allows a more robust cloud platform by giving way to separate access to the web applications by going on the rounds of a cloud-native way. This doesn’t need the positioning of IT teams to look after it always.
Where the security patches are applied
The designers and architects go for cloud-native application development by adhering to some factors. In this manner, they build and implement the specific external configuration in a stateless way.
Some of the basic design approaches related to the cloud-native application are as follows:
- Fixing Endpoints and Credentials
It is always recommended to keep the service credentials and the source and target endpoints outside the main memory scope. By following this approach, any hacker wouldn’t have any access to any of the credentials or parameters at any point in time. - Caching
Scaling is done on a very high level when it comes to Cloud-Native apps. It sometimes happens in multiple instances at some point in time. For seamlessly doing this, they use external caches such as Memcache or Redis. For a stateless design structure, the apps should never store any information for not longer than the critical time that is needed for its execution. - Personally Identifiable Information(PII)
It is not recommended to write PII information to logs. Logs are insecure to some extent as they contain information in everyday texts. They become soft targets for hackers. - Encryption of Data at Rest and in Transit
This rule applies not only for cloud-based applications but also for data center-based applications. Sensitive data should be encrypted while they are traveling through the network or when it is kept at repositories at work. The IPSec and SSL/TLS structures come in handy when it comes to conducting encryption of the data flowing through different networks. - Resources of Encryption
All the resources about encryption are fluid and dynamic. These must be cycled or renewed periodically. When the encryption is done at the application, file or the database field level, it usually provides the highest level of security. However, it is recommended for apps to use a decentralized encryption and decryption approach which will allow it to give the process at various modules which ultimately reduces the risk of getting hacked. This method ensures a better performance but also reduces the point of contact of failures that follow.Thus, these are the few authentications which all the cloud-native application builders should follow to ensure the safety of their applications that they are building. Cloud-native is, and when it is not there, it is bound to give rise to certain anomalies which will plague it to a certain level.
Anomalies in the absence of Cloud-Native Security
A tree is protected if we water its roots properly, and since the source of all software services is a cloud-based system, it ought to be protected from where it emerged. Let’s take a look at some of the vulnerabilities which the traditional approach came up with.
- Regular Vulnerabilities
A lackluster system will give rise to vulnerabilities which will affect your system regularly. A laid-back attitude will let you face you such weaknesses which is obvious. These vulnerabilities were also widespread across some of the critical websites. - Leaked Credentials
Though it can happen in a cloud-native approach too, it is more in ordinary when it comes to traditional methods. This can be prevented in a significant manner by using a cloud-native approach. - Phishing Campaigns
Phishing is, and it can only be curbed by spreading awareness and automation through Artificial Intelligence and Machine Learning for which Cloud-Native security approach will be essential. For the same things, cybercrime leads to elusive ransomware from the wrong-doers. Leaked credentials lead to such phishing campaigns and also to ransomware which sometimes the charged company is unwarranted off.
The importance of Cloud-Native Security Approach - Implementing rapid changes
Times are changing which makes the new codes to be applied even faster, but operating with an older security architecture in this phase will make it more vulnerable to non-acceptance of the changes. With DevOps being used extensively, cloud-native security approach will affect the way the new software services will be implemented.
If you want to implement new structures to your modules, then working with more unique sets of Cloud-Native Approaches will only help you. - The increasing threats
As discussed above in the approaches, the risks are increasing the implementation of new kinds of technology. The cloud-native approach will be the only path to help you ward off against such threats which looms large on you.
The problem with the traditional approach is that they won’t be able to evolve in the same manner such as the Cloud-Native security patches. - Implementing a controlled leaking of credentials
By performing cloud-native security services, credentials will only be managed in a much better manner. The lifespan of the credentials can be changed which will be difficult for the hackers to use it for their purposes. - Looming threats of Automatic updates
Sometimes these updates are exciting and in a way too exception of being a threat to the normal human consensus. What if they are a threat?
These updates get automatically fixated which makes you think of the security features that it comes with these automation makes the elements get arranged hierarchically. Thus, when the threats hit you, you believe that you are being protected, but actually, you are not which is somewhat of a broken process. Cloud-native approach eradicates this process in the most fantastic manner. - Being in a static environment
Being in a static environment for months due to the transfer of lineage from one technical base to others will lead you to many threats. Update in architectural structures takes a little time to get acquainted with. Thus, the danger to the static version is significant. Production changes to the structures attract a lot of criminals.
Therefore, a cloud-native approach to application building helps you to store them in containers, and in the time of upgrades, a need to change the entire architecture doesn’t arise. - Security Vendors
They haven’t evolved much as such. They are still basking in the pre-era of safety features which don’t have a much impact today. Technology has been on a revolutionary rise but it is high-time we reflect on how to protect it as well.We have built many things related to security which helps us to prevent the threats but what have we done to act when the threats somehow loom into our area and then threaten us. The cloud-native approach helps you to avoid as well as act against these threats at a more significant level.When it comes to Cloud security, it is a shared responsibility, the role which is shared by both the security vendor and the customer. Cloud vendors (both IaaS and PaaS) will manage the security of the cloud that your application is being hosted on, but it is your added responsibility to secure your application on the cloud by taking the respective steps.
For a fully secured data structure without any possible anomalies, you should implement the best practices and design approaches which should be carried across by your team of architects and designers. Evolution of this is undoubtedly on the rise as the threats to this growing medium increases. It will be our real task of how better are we getting to ward off the risks to the extent. Security implementation should be the topmost priority and not something which is to be kept as the last thing in the queue. It is the thing that will help you to build a level of trust among your customers. Therefore, not a single level of compromise should be entertained when it comes to this.Must Reads:
[wcp-carousel id=”10006″]